Security & Convenience: Finding the Right Balance
Too much security can lead to a decrease in convenience, causing users to bypass controls and leave sensitive information vulnerable. Too little security can result in critical information being accessible to unauthorized parties.
Information security is a critical aspect of modern society, as we rely heavily on digital systems to store and transmit sensitive information. Ensuring that this information remains confidential and secure is essential to maintain trust and protect against cyber threats. However, achieving a proper balance between security controls and convenience is a major challenge.
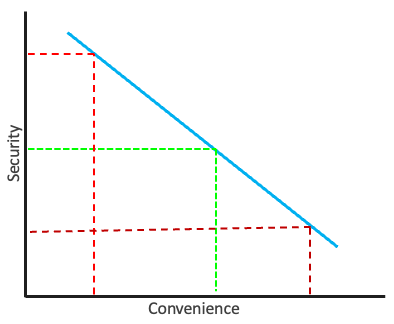
On one hand, security controls are necessary to prevent unauthorized access and protect sensitive information. For example, strong passwords, two-factor authentication, and encryption are all security measures that can help keep information secure. However, as the number of security controls increases, the user experience becomes increasingly inconvenient. For example, a user might have to remember multiple passwords or enter long codes every time they want to access a system.
On the other hand, convenience is an important factor to consider because it can affect user behavior and determine whether security controls are effective. For example, if users are frustrated by the inconvenience of logging into a system, they might be more likely to write their passwords down where they can be easily accessed. Similarly, if users find it too difficult to navigate a complex security system, they may be more likely to seek out alternative, less secure solutions.
The key to effective information security is finding a balance between security controls and convenience. Too much security can lead to a decrease in convenience, which can result in users bypassing the controls and leaving sensitive information vulnerable. On the other hand, too little security can result in critical information being easily accessible to unauthorized parties.
To ensure a balance between security controls and convenience, you can take the following steps:
- Conduct a risk assessment: Start by assessing the risks to your sensitive information, and determine what level of security is required to mitigate those risks. This will help you determine the right balance between security controls and convenience.
- Choose the right security measures: Choose security measures that are appropriate for your risk level and provide the necessary level of protection. Ensure that the measures are both effective and convenient for users.
- Train users: Provide users with the training and resources they need to understand and use security measures effectively. This will help them understand the importance of security controls and why they need to follow them.
- Monitor user behavior: Regularly monitor user behavior to ensure that security measures are being used correctly. This can help you identify any areas where users are struggling with convenience and make changes as necessary.
- Continuously review and update: Regularly review and update your security measures to ensure that they are still effective and relevant. This will help you maintain the balance between security and convenience over time.
- Consider user feedback: Encourage users to provide feedback on the security measures in place, and use their feedback to improve the overall experience. This can help you identify areas where you can improve convenience without sacrificing security.
In conclusion, finding a balance between security controls and convenience is essential for effective information security. By striking a balance, organizations can ensure that their security measures are both effective and usable, reducing the risk of cyber attacks and protecting sensitive information. This requires careful consideration of the security measures being implemented and a clear understanding of the impact they will have on users. Only by taking a balanced approach can organizations ensure that their information security systems are effective and usable and that sensitive information remains secure.
